Tenacy allows you to manage your security incidents. Find out how to create and manage them.
Summary
1.
1.1.
1.2.
2.
3.
4.
1. Reporting an incident
1.1. By a contributor
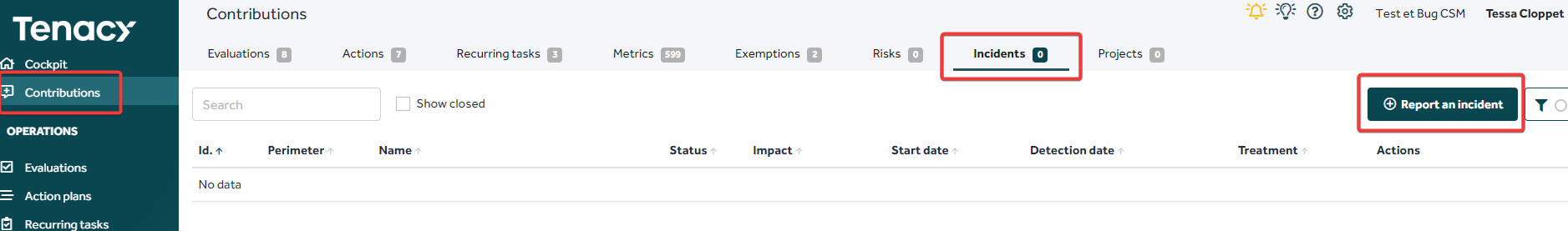
Your contributors can report an incident via the “Contributions” tab

- Name: incident name
- Perimeter: specify the perimeter where the incident occurred
- Identifier: if you do not add an identifier, the solution will generate one automatically
- Start: date the incident is declared
- Detection date: date the incident occurred
- End date: date the incident should be closed
- Status: Status of the incident. You have the choice between 7 different statuses
- Labels
- Reporter: person who reported the incident
- Impact: arbitrary assessment of the impact of this incident on your organization
- Description
The "History" tab allows you to add details regarding the sequence of events.
The “Analysis” tab allows you to add comments, images, etc.
1.2. By a pilot
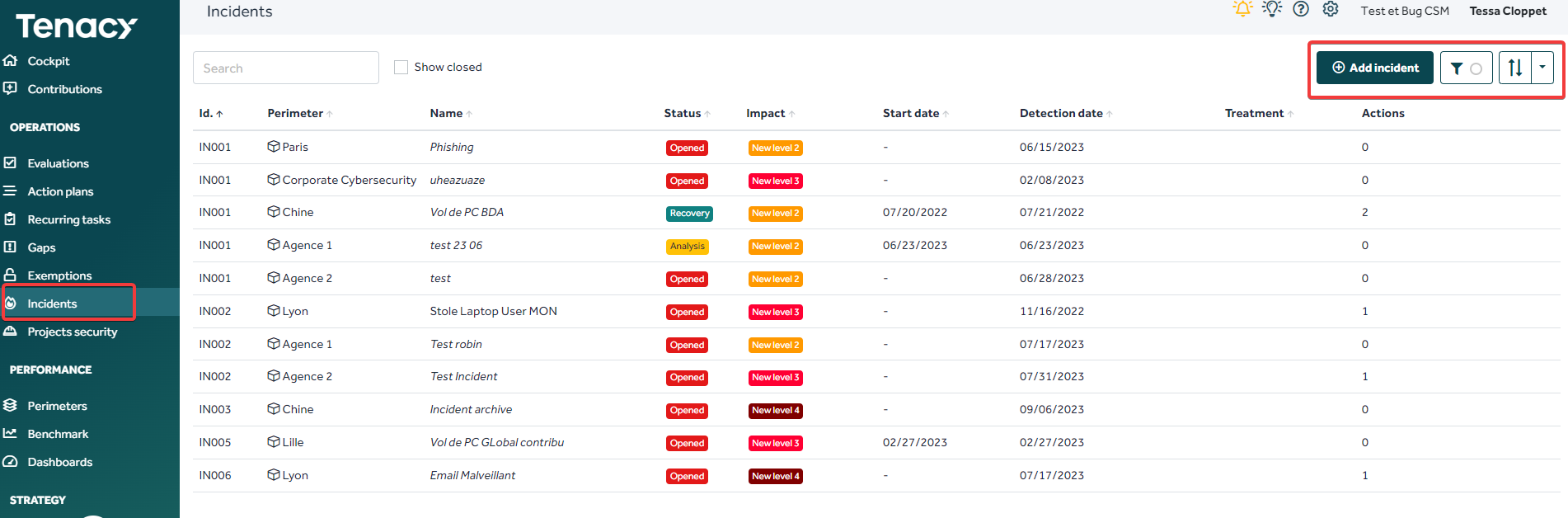
You can also report incidents via the "Incidents" tab directly.
You can report an incident:
- by clicking on the “Add an incident” button as seen previously
- or by Excel import.
2. Incident management
As a pilote you can manage your incidents in the “Incidents” tab.
You have the possibility to:
- “Parameters” tab: update the incident status
- “Activity”, “Files” and “Analysis” tabs: record notes/evidence about the incident
- “Actions” tab: link to actions
3. Take a decision through actions
🤔 Before taking any decision the incident owner can put up an action plan.
💡 To facilitate your management of incidents you can create user groups.
Implementation of an action
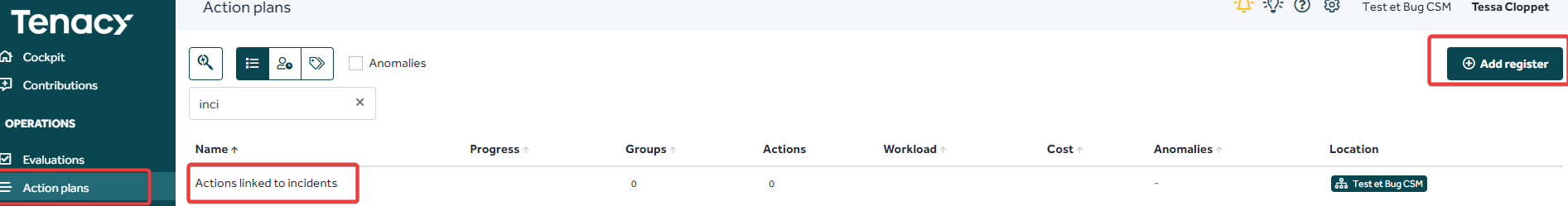
💡 A action register related to incidents actions will allow you to facilitate monitoring and reporting.
Action plans > Add a register
In your incident > "Actions" tab > Add an action. You will then be able to add the register you create.
🔎 Once the actions have been completed, the owner of the incident will be alerted in the Review section of Tenacy.
3. Reporting
You can create dashboard blocks on these incidents and report on: the number of incidents, the number of critical incidents, the processing time, etc.
Explanatory video - AugmentedCISO version but the settings are unchanged.